8. Cybersecurity Cases on Global Perspectives
April 29, 2022 lectured and wrtitten by Aylin BİLEN
About Aylin BİLEN
In this week's lecture, Aylin Bilen, who has been studying for her master's degree in cybersecurity from an international perspective was the guest instructor. She is an expert in the International Relations Department of the Presidency of the Republic of Türkiye, Digital Transformation Office. We discussed cybersecurity and ethics problems, cases, and possible solutions.
"Companies spend millions of dollars on firewalls, encryption and secure access devices, and it's money wasted; none of these measures address the weakest link in the security chain." —Kevin Mitnick
As of January 2022, there were 4.95 billion internet users worldwide; %62.5 percent of the global population.**
History of Internet
In 1969- the Defense Department (USA)started a modest connection of a few computers called ARPANET, and
In 1972, the codes for exchanging data (TCP/IP) were created to constitute a rudimentary internet capable of exchanging packets of digital information.
In 1984, the domain name system of internet addresses starts, and the first computer viruses were created about that time.
The First Computer Virus
The Creeper virus was first detected on ARPANET, the forerunner of the Internet, in the early 1970s. Creeper was an experimental self-replicating program written by Bob Thomas at BBN Technologies in 1971.
In 1989, The World Wide Web begins
In 1998 Google the most popular search engine was founded.
In 2001 the open-source encyclopedia, Wikipedia, begins.
In the late 1990s, businesses begin to use the new technology to shift production and procurement in complex global supply chains. Only recently has there been the bandwidth and server farms to support “cloud computing” in which companies and individuals can store their data and software on the Web.
In 1998 ICANN (the internet corporation for assigned names and numbers) was created, and the US government only began to develop serious national plans for cyber security in the past decade.
In 1992, there were only a million users on the internet; within fifteen years that had grown to a billion. In its early days, libertarians proclaimed that “information wants to be free” and portrayed the internet as the end of government controls and the “death of distance.”
Now; in practice, governments and geographical jurisdictions play a major role, but the domain is also marked by power diffusion.
What are Cyber and Cyberspace?
The word «cyber» comes from the Greek word «Kubernetes» which means steersman → cybernetics
Cyberspace is a word describing the invisible and intangible space in which humans communicate via computers.
With the emergence of the concept of cyberspace; the concepts of time and place have started to change.
The geography of cyberspace is much more mutable than other environments. Mountains and oceans are hard to move, but portions of cyberspace can be turned on and off with the click of a switch.”*
Cyberspace is a transnational concept.
Cyberspace — No more talking about physical borders.
Although we talk about an intangible space, we communicate in this space with computers and software. These are developed by humans and these physical machines are located in the real world.
“Cyberspace is an operational domain framed by the use of electronics to exploit information via interconnected systems and their associated infrastructure. Power depends on context, and cyber power depends on the resources that characterize the domain of cyberspace.” — Joseph Nye
Cyber Security:
With the end of the Cold War in 1990 following the dissolution of the Soviet Union, new concepts of security emerged.
In the 21st century, the concept of security is more complex than ever. With smartphones, tablets, and personal computers our daily lives are getting more digital every day.
Besides opportunities, we face some new threats. Security problems in digital environments are one critical example.
Three important components of the internet: are computer, user, and network. The weakest link principle says: “A chain is only as strong as its weakest link”.
Information flows cause security problems.
States started to use the opportunities of cyberspace by establishing critical infrastructures, collecting intelligence, and integrating technology in defense.
Developing countries now transfer the services of all sectors to cyberspace and therefore critical information.
Cyber Attacks:
The internet is messy, interconnected, and complex. Data is everywhere, cyberattacks happen all the time, and damage to all sorts of equipment and systems is inevitable.
Prominent Cyber Attacks
In 2007, Estonia suffered a distributed denial-of-service attack that was widely attributed to “patriotic hackers” in Russia who were offended by Estonia’s movement of a World War II monument to Soviet soldiers.
In 2008, shortly before Russian troops invaded, Georgia suffered a denial of service attack that shut down its internet access. (In both instances, however, the Russian government seems to have abetted the hackers while maintaining “plausible deniability.”)
Other forms of hard power within cyberspace include the insertion of malicious code to disrupt systems or steal intellectual property. Criminal groups do it for profit, and governments may do it as a way of increasing their economic resources.
China, for example, has been accused of such activities by a number of other countries. Proof of the origin or motive of such attacks is often very difficult as attackers can route their intrusions through servers in other countries to make attribution difficult.
For example, many of the attacks on Estonian and Georgian targets were routed through American servers.
Well, has the situation changed today? Let’s look at the Russia-Ukraine War we witnessed from a cyber perspective.
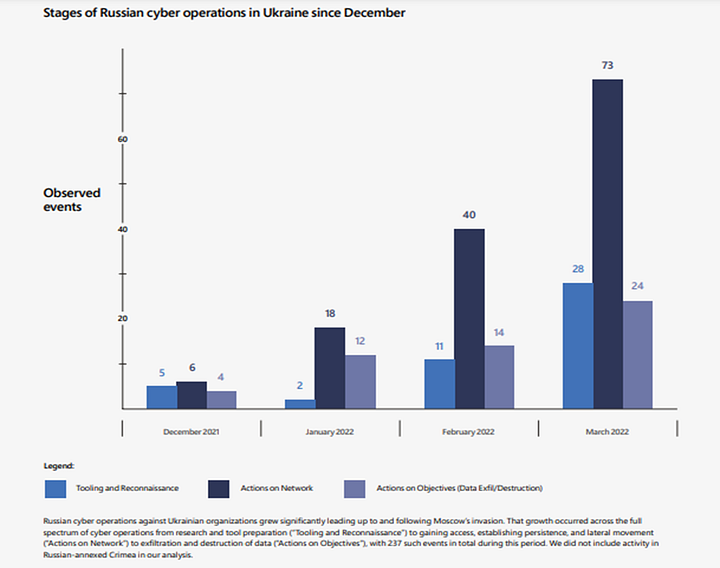
Russia’s Recent Cyber Attacks in Ukraine
According to Microsoft’s Report; “More than 40% of the destructive attacks were aimed at organizations in critical infrastructure sectors that could have negative second-order effects on the government, military, economy, and people. 32% of destructive incidents affected Ukrainian government organizations at the national, regional, and city levels.”
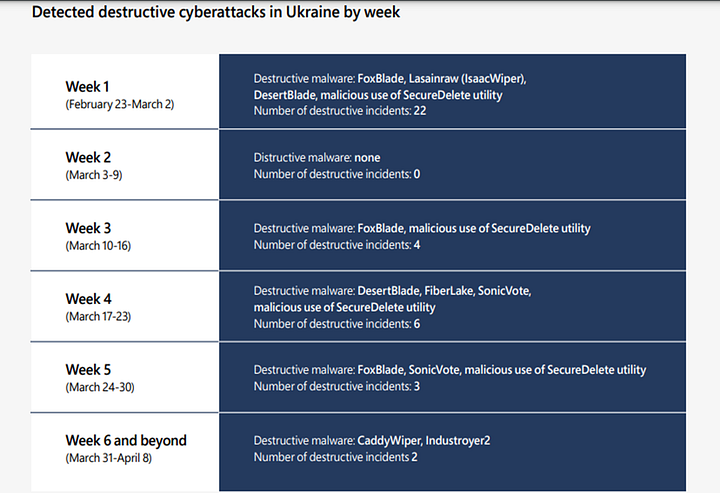
The targeting of critical infrastructure raises particular concern as this infrastructure is essential for the survival of the civilian population. Attacks on infrastructure such as energy, water, healthcare, financial institutions, transport, and communication services can have devastating consequences on the civilian population. NGOs responding to the humanitarian needs of the population in Ukraine and neighboring countries are targeted by cyberattacks in order to disrupt their activities.
Beyond the risks to critical infrastructure and civilian objects, cyberattacks sow distrust and limit access to accurate information or spread false information. They can also be highly disruptive and create a sense of fear and uncertainty and even lead to the eventual displacement of people.
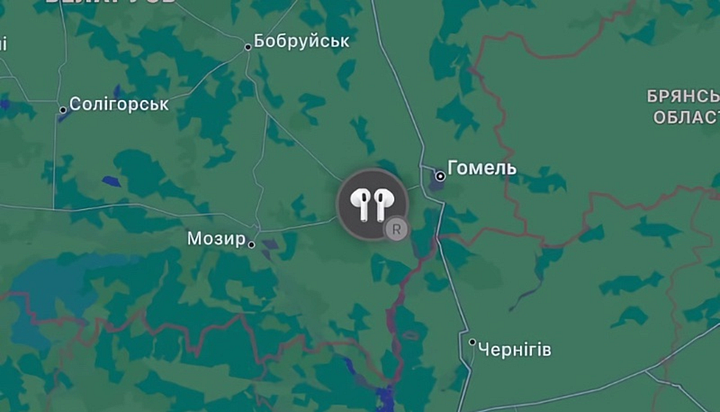
Apple’s FIND MY FEATURE: Russia- Intelligence
A Ukrainian man has been tracking the redeployment of Vladimir Putin’s forces via a pair of wireless earphones stolen from him by invading troops.
Vitaliy Semenets’s Apple AirPods were looted from his home in Hostomel, near Kyiv, soon after the war began as Russia tried to take the Ukrainian capital. As Russian soldiers pulled back from Kyiv this month, Mr Semenets followed his earphones on online maps as they were taken across the border into Belarus, ending up near the city of Gomel.
He has since been using Find My — a location-tracking feature available on all Apple products — to follow the troops on their 550-mile retreat across the country.
The Role of NATO
Following World War II, the states were in search of cooperation in economic and social areas as well as the security area. North Atlantic Treaty Organisation was established on April 4, 1949 with the signing of Washington Treaty. One of the objectives of the establishment of NATO was to prevent the threat of socialism from the Soviet Union at that time. There was a bipolar world system between the two great Powers: the USA versus the Soviet Union.
The period of Cold War following World War II, has established the basis for the new types of threats such as ballistic missiles and cyberattacks. It was quite difficult to detect the origin of these kinds of threats. Because during the Cold War, seemingly, there was no actual war. But the intelligence mattered so much. After the Cold War, the concept of security changed and new types of threats emerged. Cyberattacks, cyber espionage, and cybercrime are among those threats.
Cyber Defence and NATO
Cyber defense is part of NATO’s core task of collective defense. Cyberspace has been acknowledged as one of the domains of operation in 2016 by the Allies, in addition to air, land, and sea. Starting from the 2010 Strategic Concept document of NATO cyber security issues are addressed in the strategies of NATO.
NATO offers training and capacity-building activities and exercises. NATO’s main objective in cyber defense is to protect its own networks and enhance resilience across the Alliance. NATO’s 2030 Agenda; stronger cyber defense is aimed.
NATO CCD COE:
NATO Joint Cyber Defense Center of Excellence (CCD COE) is an international military center established in Tallinn, Estonia, on 14 May 2008 to increase NATO’s cyber defense capacity.
The Center, which is currently sponsored by 11 NATO countries, and our country is nearing the end of its membership process; It carries out a wide range of activities in Cyber Security, both technical, legal, and international relations.
Among the prominent projects of NATO CCD COE; “The Tallinn Manual on the International Law Applicable to Cyber Warfare” study and the annual “International Conference on Cyber Conflict (CyCon)” and the Locked Shields International Cyber Defense exercise can be cited as examples.
Why is this center in Estonia?
Before 2007, Estonia had a reputation for being “the most wired state in Europe”. In fact, when the country gained independence in 1991, only half of the population had access to basic telephone lines.
However, the new Estonian government saw the lack in this area as an opportunity and encouraged R&D work in the fields of information technology and telecommunications. As a result of these studies, the country has made many innovations. For example, the software used in the preparation of Skype was of Estonian origin. In 2005, for the first time in the world, the Estonian government offered its citizens the opportunity to vote electronically.
In this period, nearly 60 percent of the people were in need of the internet for a significant part of their daily needs. About 96 percent of banking transactions in the country were carried out online. However, in this whole process where important breakthroughs were experienced, the information technology infrastructure was given a weak appearance because the Estonian government did not do the necessary studies on internet security and cyber defense.
In the Final Stage; the third week of the attacks, Estonia faced the heaviest cyberattacks on the night of 9 May to 10 May. The attacks, containing up to 4 million packets of information per second, targeted the Estonian banking system. The systems of Hansabank, the largest bank in the country, could not withstand the attacks and had to shut down its servers.
How it Started?
The parliament’s decision to remove the Bronze Soldier statue in Tallinn square not only drew strong reactions from the ethnic Russian minority, but Russia also reacted strongly to the decision. Finally, on the evening of April 26, 2007, a large-scale cyber-attack of unknown origin had begun.
The attackers were using a cyberattack method known as Distributed Denial of Service (DDos). In other words, in the first stage, many computers were seized and turned into zombie computers. Most of the time, users were not even aware that their computers were hacked. In the second stage, a network called Botnet was created from these zombie computers that were seized and it was ensured that they systematically attacked the determined web pages.
White-Grey-Black Hats Hackers
Basically, white hat hackers hack for good reasons to identify loopholes in the existing technology and fix them before black hat hackers discover them.
Black hat hackers hack for bad reasons and some of their activities include stealing credit card information and accessing email accounts.
Other hackers which are in-between hack just because they are able to or which cause chaos and not because they have any real agenda.
Hack-Back: Slippery Slope!
HACK-BACK:
Private sector “hack back” means non-government organizations taking intrusive action against a cyber attacker on technical assets or systems not owned or leased by the person taking action or their client. There was a policy proposal in 2021 and before. However, there are challenges:
In most cases, it’s extremely difficult to be certain that attacks are being correctly attributed, as attackers can use deliberately deceptive techniques to divert blame elsewhere.
Legitimate research could accidentally trigger an unnecessary hack back. (can be perceived as a threat).
The path to oversight is blurry, with non-specific plans of how it could be managed to make it practical and minimize the potential for risks and abuses. At this current moment, there are a lot of questions around a potential framework and system
The issues of practical execution also raise questions around who will bear the responsibility and liability if something goes wrong.
Cyber Security and Ethics
Social media companies have had only limited success in suppressing terrorist media and hate speech. This is likely to continue in spite of the best efforts by these companies.
Terrorists love encryption. They are keen users and understand how to use it effectively. There are arguments that governments should be given a “back door” to decrypt messages.
Dark Web:
The Dark Web is a collection of private internet sites that can only be accessed with a private web browser. Used to keep internet activity anonymous and private; which is useful for both legal and illegal practices.
Deep Web:
The Deep Web remains below the surface and makes up almost 90% of all websites. This is the submerged part of the iceberg and is much larger than the surface web.

In fact, this hidden network is so large that it is impossible to find out how many pages or sites are actually active at any given time. Payments are made in cryptocurrencies.
After all, we are faced with many problems, in a news we learned while we were still in class, we learned that Google Chrome is the target of hackers.
Black Hat & White Hat Hackers
DeepWeb — DarkNet
Misuse of the internet
Disinformation, propaganda
Organization and management of terrorist acts
As a result of our discussions in the classroom, we came to the conclusion that we can only solve these problems with legal regulations.
Next week we will have a quiz to summarize the last three weeks. We will consider the stakeholders of the digital ethics ecosystem.
References:
Last updated


